1st step Authentication
Mechanism which permits to verify the identity of the parties involved in a call.
Based on a challenge-response type of protocol, which uses a particular authentication key K.
The K key is unique for each terminal: it is stored in a protected way in the terminal itself.
A network element called Authentication Center (AUC) contains the K keys of all of the authorized terminals.
The K key never travels over the air.
Different authentication processes are available:
User authentication
Terminal authentication
Infrastructure authentication
Reciprocal authentication
Terminal Authentication:
This mechanism allows the infrastructure to verify the identity of the terminal that asks permission to register and operate in the network.
fig.1
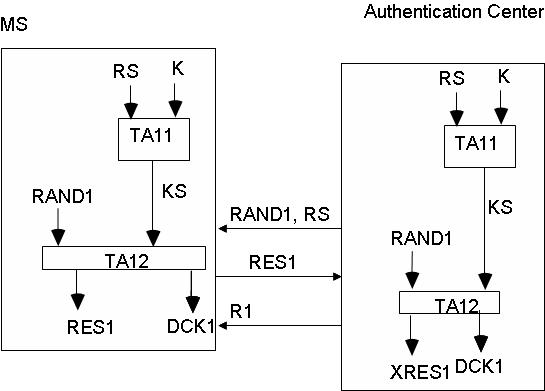
The AuC sends the RS and RAND1 values, generated randomly, to the terminal.
The terminal processes the RES1 response and sends it to the AuC.
The AuC compares RES1 with the locally generated value and responds (R1) with the acceptance or rejection of the authentication.
Infrastructure Authentication:
Mechanism that allows a terminal to verify the authenticity of the network before registering.
It prevents attacker from using equipment that simulates a TETRA network to acquire sensitive data.
In this case, it is the terminal that challenges the infrastructure to prove its identity. The process involves the usual K key.
The terminal begins the registration procedure only if the process ends with acceptance of the network.
fig.2
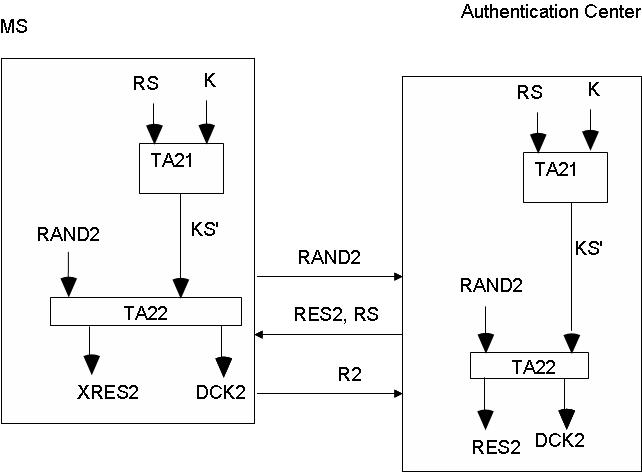
The terminal launches the challenge, sending a random RAND2 value to the AuC
The AuC generates an RS seed and processes the RES2 response. Both values are sent to the terminal.
The terminal processes XRES2 and compares it to RES2.
The terminal responds (R2) with authentication successful or failed.
Mutual Authentication:
Started by the network or by the terminal, it consists in the reciprocal authentication of the two entities.
The terminal or network, while responding to the authentication request, requests it in its turn.
Starting from the K key, two different session keys, used in the two processes, are generated.
fig.3
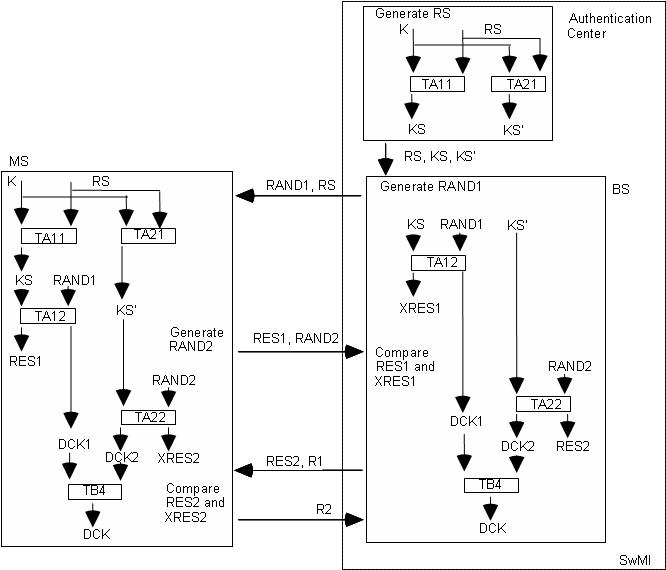
Both unprotected (no encryption) terminals and terminals that use security mechanisms can operate in a TETRA network.
For this reason, the registration (which follows any authentication) is not encrypted.
The same thing also occurs for synchronization messages and for the broadcast PDUs containing the system parameters.
During authentication processes, beginning from the RS and RAND values, the response to the challenge is generated, as well as a DCK key.
The DCK key is used as a dynamic key for the encoding of the data over the air.
2nd step Encryption:
Encryption is the technique of making the meaning of a message unintelligible. Even if the message is intercepted, it cannot be used.
A message is encoded using an algorithm agreed upon between sender and receiver, which uses an encryption key.
The encryption algorithms are divided into two large categories:
Private key algorithms
Public key algorithms
Private Key Algorithms:
These algorithms are characterized by the fact that the same key is used to encode and decode a message.
The main private key algorithms are DES, Triple DES and IDEA.
The greatest advantage of private key algorithms is their simplicity and speed.
Long keys can be used to discourage brute force attacks.
On the other hand, these systems require a large number of keys (one for each group of users that wish to communicate in protected mode).
However, the main disadvantage is the need to exchange the encryption key between sender and receiver in secure mode.
If the key is intercepted, it is possible to decipher all of the messages exchanged between user1 and user2.
Public key algorithms:
For these types of algorithms, each user has a pair of keys:
public key – can be known by everyone
private key – known only by the owner
Public key algorithms, such as RSA, radically eliminate the key distribution problem.
It is extremely difficult to find the corresponding private key from the public key.
On the negative side, these algorithms are slower than private key algorithms and require greater computational power.
Hybrid Algorithms:
The message is encoded with a symmetric algorithm.
The key is transmitted in secure mode using a public key algorithm.
IDEA Algorithm:
The basic algorithm used for call security within the TETRA system is:
(International Data Encryption Algorithm)
Symmetric private key algorithm
Secure key exchange mechanisms
The keys never travel unencrypted over the air (which is the most critical path)
Proposed in 1992, IDEA is used especially in real time communication systems, thanks to its speed
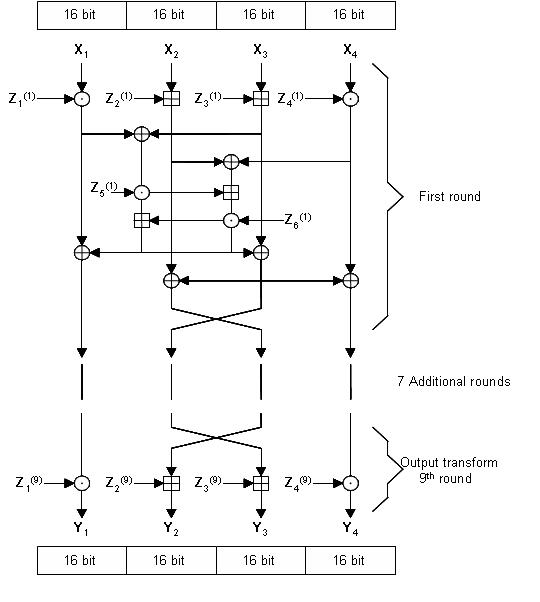
IDEA uses a 128 bit key to encode 64 bit blocks at a time, according to the diagram shown in the figure.
fig.4
Encryption in the TETRA System:
Two different types of encryption are defined for the TETRA system:
Air Interface Encryption - this concerns the air segment of the communication system; the network carries out the encoding and decoding of signaling and traffic
End-To-End Encryption - this concerns the user-user segment of the communication system; the terminals and the dispatchers encode and decode the traffic.
The encryption schemes are completely separate and independent:
AIE is agreed upon between terminal and infrastructure.
E2EE is transparent to the TETRA infrastructure and is agreed upon only at the user level.
The user authenticated on a network that supports AIE can enable E2EE in order to have a double level of security: a double encoding is carried out in the air segment and the traffic travels in the infrastructure in protected mode.
Air Interface encryption makes the data secure over the segment from MS to the Base Stations.
The keys are injected into the terminals and entered in the network.
All data travelling over the air (signaling as well as speech and data traffic) are encoded.
Static encryption (SCK mode)
used when authentication is not necessary
infrastructure and terminals share the same set of keys (fixed)
the key to be used is established at the SCN – Local Terminal level
the ID of the established key is sent to the terminals through specific signaling on broadcast messaging (SYSINFO)
the SCK key is also used by the BS in fallback
Dynamic encryption (DCK mode)
Used where authentication is necessary
The DCK key is derived during the authentication process, beginning from the K key.
The DCK key is unique for each terminal.
The keys are updated through specific signaling on broadcast messaging, or individually through a specific OTAR (Over the Air Re-keying) protocol.
In order to obtain the encoding sequence, the SCK key is combined with some parameters of the BS:
Colour Code
Location Area ID
Control channel Carrier Number
Initial Value (IV), which is obtained starting from the Frame Number, Multiframe Number and Hyperframe Number values
The TEA1 algorithm on BS is realized through a specific FPGA to be inserted on the BB card of the TRX.
The AIE encryption key can also be used to protect the identify of the called user.
On the BS, the TA61 algorithm is implemented at the EIU Crypto level, in the SC cardframe.
1 EIU ENCRYPTION with TEA1 algorithm (code xxxxx) to be inserted in TSU cardframe
1 FPGA CRYPTO (code xxxxx) inserted on BB card of each TRX.
1 GPS I/O card (code xxxxx) to be inserted in the TSU cardframe; the card's secure memory contains the seed used to reconstruct the true SCK key, starting from the one (encrypted) supplied by SCN.
ну в общем там ещё много чего есть... тяжко дёргать...
если софт появится дайте знать... оч интересно... поглядеть на енто, а главное послушать...





